- Services
- Industries
- Automotive
- Battery
- Building inspection
- Fire alarms system testing
- Household appliances
- Installation materials
- Industrial machinery
- IT & audio video
- Laboratory, test & measurement
- Lighting equipment
- Maritime, oil & gas
- Medical & healthcare equipment
- Military & aerospace product testing
- Wireless & telecom
- Resources
- About
- Blog
- Events
In the past years, and as a result of the pandemic, we’ve seen an increase in the number of Internet of Things (IoT) brought into our homes. And now, after Christmas, most of us will probably have received new IoT such as connected toys, IP cameras, smart home appliances and – to help us with our New Year resolutions – connected wearables to motivate some additional training.
And even though most of us aren’t computer wizards, we are capable of connecting these new gadgets to our home Wi-Fi easily and to install the relevant apps on our smart phones. This is all thanks to manufacturers who have done their outmost to make everything as easy as possible for us – almost like magic.
But magic comes with a price…
IoT can reduce your cyber security
The price we pay come in the form of dramatically reduced cyber security. The reduced security not only applies for the connected toy or smart home appliance in question but for our entire network and everything connected to it.
The reason for this is the Universal Plug and Play (UPnP). UPnP performs a range of operations, but simply put it is the functionality which allows the different devices in a network to discover each other and to connect both within the local network and to the world outside. Although this might sound good, the problem is that UPnP does not perform any authentication of what gets connected. This creates a risk of someone addressing your IoT directly through the internet and gaining access to or manipulating the unit.
Read also: Cyber security becomes a mandatory CE marking requirement for wireless equipment
What about the firewall?
Although no IoT is directly connected to the internet, but through a router that has firewall protection, there is still a catch. During the automated installation, the IoT creates a “hole” in the firewall to allow traffic to enter the IoT. While this “hole” may have been intended for legitimate traffic between the IoT and the server, it can be misused by others to gain access to and control over your IoT – and hereby your network.
Your PC could be the target
It is unlikely that any person would want to spend time gaining control over your robot vacuum, but the purpose of the attack is not to be able to control your IoT, but to use the device in further attacks or to get access to other parts of your network, such as personal computers (PCs).
Furthermore, the method employed to gain access to your devices is not manual, but rather an automatic search which conducts scanning of thousands of networks at all hours of every day, so any IoT constitutes a potential target.
Which preventative measures can you take?
There are a few things you can do to protect your IoT from becoming a target device for cyber security attacks:
- Use strong passwords and put all IoT on the guest network if possible.
- Disable the UPnP. To do this you log into the router as described in the user manual or printed on the router itself. You do this by finding the UPnP and choosing ‘disable’ or ‘OFF’.
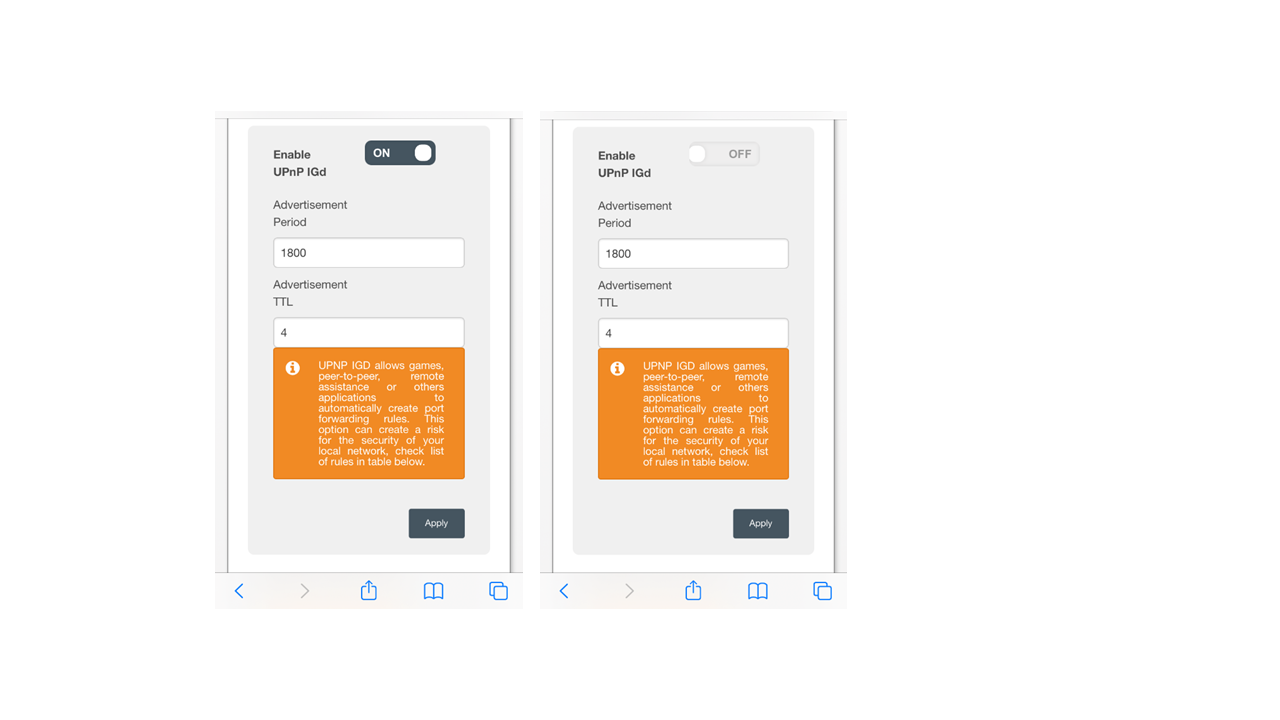 Read also: Cyber Security and the Internet of Things
Read also: Cyber Security and the Internet of Things
Geir Hørthe
Geir Hørthe is responsible for the Nemko cyber security initiative. He has worked at Nemko for more than 30 years, in the capacity of test services, lab manager of safety, ATEX and medical departments. He has also been Managing Director at the Nemko office in London for two years. After he returned to Norway, he held...
Other posts you might be interested in
New Cyber Security Requirement for CE Marking: What You Need to Know
September 27, 2021
//
Cyber security
Top 10 FAQs on Cyber Security and CE Marking: What You Need to Know
May 20, 2022
//
Cyber security
How IoT devices, even washing machines, can be used for hacking
February 7, 2024
//
Cyber security
